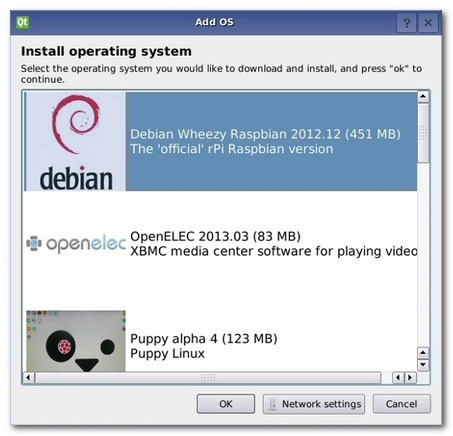
I was scouring the internet to find additional resources to utilize in my classroom when I came across BerryServer. It is a website developed by Alexander Goldcheidt which has a very large collection of additional BerryBoot Images. Once you have BerryBoot installed, follow the instructions below.
Once you have the image file (.img) put that image file on a FAT32 formatted USB device, then in Berryboot main screen hold down your mouse button over “Add OS” and select “Install from USB stick”, choose the OS image(s) from the USB device and wait the copy process, reboot the Raspberry Pi by clicking the exit button. That’s it, wait to Berryboot boot and select the new OS image.