A Comprehensive Theoretical Wireless Security Project
Updated 11/01/2018 1:30am
Objectives
By the end of this course and the completion of this project, students should be very knowledgeable in theory and practicality of the five objectives below.
W01) The differences between wireless security and wired security
W02) Designing security solutions in wireless network systems
W03) Data-oriented and voice-oriented wireless security systems
W04) Advanced wireless network security systems
W05) Enabling and configuring a wireless network systems
Pre-Lab Survey
Please follow this link to complete a pre-lab survey. There are no right or wrong answers. This is simply to assess your knowledge of wireless security prior to completing this project. ((This survey is only for Spring 2019 students!))
The Project
Red Team vs Blue Team: The Red Team vs Blue Team is a scenario-based, theoretical lab experience. The goal is to put together items learned during your Wireless Security course and apply them in this theoretical environment.
-
- Students will place themselves in a group on D2L
- Groups should be no less than 4 students and no more than 6
- Establish roles within the group (2-3 Red Team Members, 2-3 Blue Team Members)
- The Red Team – White-hat hackers that attack an organization’s digital infrastructure as an attacker would
- Research the tools listed in each step
- Discuss and document the purpose of the tool and the vulnerability the tool can exploit
- Discuss and document which tool would be most effective (speed, stealth, etc.)
- The Blue Team – Design defensive measures against such red team activities
- Research the tools listed in each step
- Discuss and document how you would prevent each tool from exploiting a wireless network
- Discuss and document how you would recover from each exploit
- Findings – Submit (1) research paper and a PowerPoint with a minimum of 3 citations
- Your research paper should discuss the effectiveness of red team blue team exercises
- Your PowerPoint should cover identify the team members, research methods, and the effectiveness of red team blue team exercises for wireless security.
The Project
Step 1 – Research Wireless Auditing Tools (2 hours)
Research Fern Wifi Cracker and Wifite based on your selected role. These are two tools that can be used for wireless auditing and perform essentially the same task. One is GUI, the other command line.
Step 2 – Research Information Gathering and Vulnerability Analysis Tools (2 hours)
Research SPARTA and nmap based on your selected role. These are both tools that can be used for information gathering and vulnerability analysis. They perform essentially the same task. One is GUI, the other command line.
Step 3 – Compare and Contrast Pentesting Platforms (1.5 hours)
Research and compare (2) penetration testing platforms: Kali vs ParrotS,
The objective is to discover:
- Which platform has the tools you need to conduct your research
- What hardware the platform can be installed and run on (PC, Mac, Raspberry Pi, Tablet, Phone, Virtualized, etc.)
- Can the tools be automated on the platform (Bash script, Python, cron job, etc.)
- At least five more
Step 4 – Research One Exploit (1 hour)
Step 1 was researching tools for wireless auditing and how they function. Step 2 was to research tools that can be used to discover information about a network once an attacker has gained access to a network. Step 3 was identifying which penetration testing platform would be best based on the tools mentioned above. Step 4 is to research the actual exploit, what causes it, and how you can prevent it.
If research is conducted thoroughly, your research paper will be no more than 4-5 pages when double-spaced and properly formatted. You are not required to complete an abstract. However, if you decide to conduct further research in this area and have it published, you will have met almost 75% of the requirements. Below is an example of the expected outcome.
Research Expected Outcome
GoLismero is an open source software framework for security testing. It is geared towards web security, however, it can be expanded to other types of scans. GoLismero can run security tests and manage other well-known security tools such as OpenVas, Wfuzz, SQLMap, DNS recon, and robot analyzer while taking their results. The feedback from all of the tools are merged and a report is generated. All of this can be automated and run on either pentesting platform, however, Kali is the best choice as Parrot Security implements Firejails and AppAmour which cause a malfunction when calling other applications.
GoLismero is run from the CLI by typing “golismero scan <target> -o <output file name>” where target can be an ip address or a url and the output file can be any format you choose. By choosing html as the file format, you can receive an easy to comprehend snapshot of the environment and vulnerabilities. See exhibit A. A potential exploit from a website vulnerability would be cross-site scripting.
Cross-site Scripting (XSS) attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user in the output it generates without validating or encoding it. According to Williams et al. (2018), the best way to defend against cross-site scripting is to set the HTTP Only flag on your session cookie and any custom cookies you have that are not accessed by any Javascript you wrote. This cookie flag is typically on by default in .NET apps, but in other languages, you have to set it manually.
References
Williams, J., Manico, J., & Mattatall, N. (2018). XSS (Cross Site Scripting) Prevention Cheat Sheet – OWASP. Retrieved November 1, 2018, from https://www.owasp.org/index.php/XSS_(Cross_Site_Scripting)_Prevention_Cheat_Sheet#XSS_Prevention_Rules_Summary
PowerPoint Expected Outcome
- List each team members
- Who was on the red team, who was on the blue team
- How were the roles determined
- What research method did you choose
- Observation – Did you watch Youtube videos
- Surveys – N/A
- Interviews – Did you talk to industry pentesters
- Focus Groups – N/A
- Experiments – N/A
- Secondary Data Analysis – Did you review the results of others
- Mixed Methods – Did you use a combination of research methods
- What is the effectiveness of red team blue team theoretical exercises for wireless security
Step 5 – Proofread and Submit
Proofread your research paper for spelling and grammatical errors, typos, and punctuation errors. When complete submit to the appropriate drop box as follows:
Team Project Report 1 – Submit the results of your research and discussions for steps 1, 2, & 3
Team Project Report 2 – Submit your research for step 4 as described
Team PowerPoints – Submit PowerPoints
Team Evaluation – Submit Indiviual Evaluations o
Post-Lab Survey
Please follow this link to complete a post-lab survey. There are no right or wrong answers. This is simply to assess your knowledge of wireless security after completing the course and lab. ((This survey is only for Spring 2019 students!))
Future Work (Possibly Capstone Fall 2019)
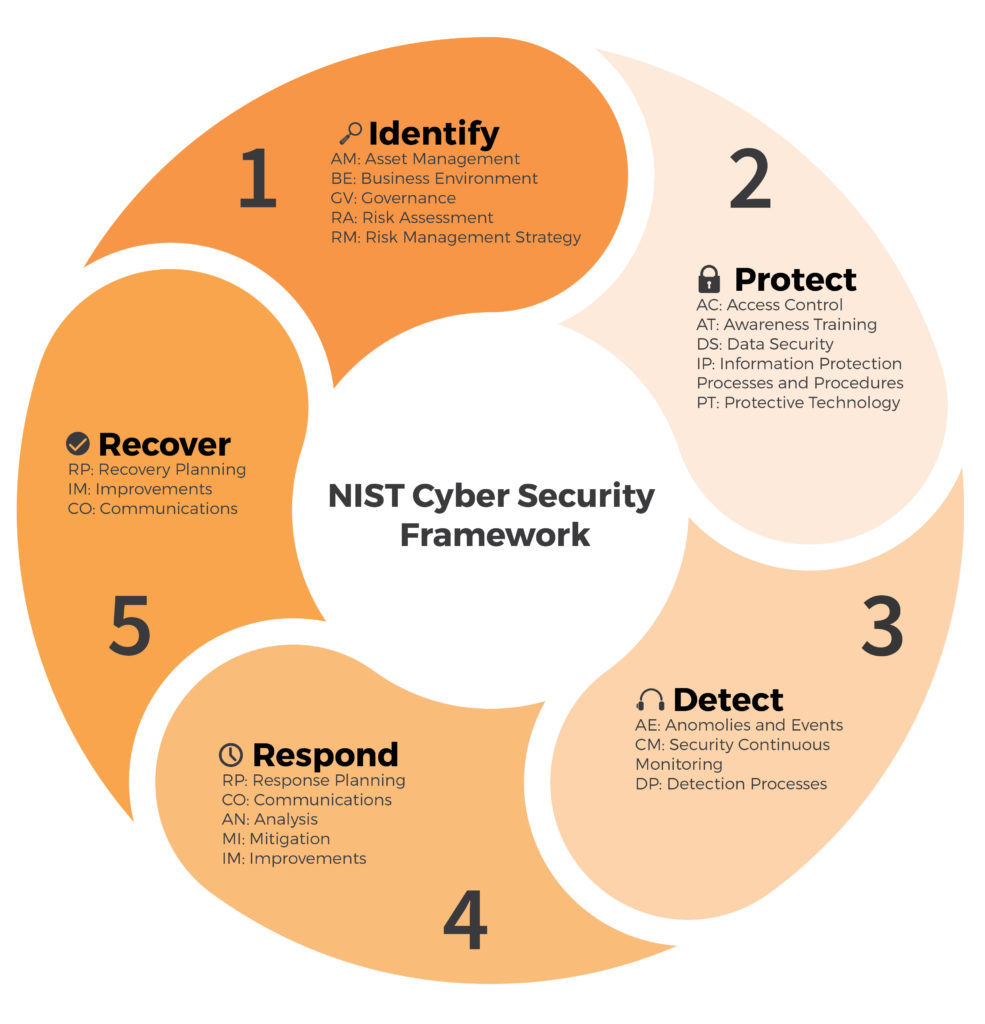
Use the NIST Cybersecurity Framework to put it all together and be prepared to present to the class and possibly outside employers in the cybersecurity field. Create a 10-page PointPoint in which you address how you would use the NIST Cybersecurity Framework to protect a real organization based on this lab.