A Comprehensive Practical Wireless Security Project
Updated 10/30/2018 4:30pm
Objectives
By the end of this course and the completion of this project, students should be very knowledgeable in theory and practicality of the five objectives below.
W01) The differences between wireless security and wired security
W02) Designing security solutions in wireless network systems
W03) Data-oriented and voice-oriented wireless security systems
W04) Advanced wireless network security systems
W05) Enabling and configuring a wireless network systems
Fall 2018 Lab Progress Survey
Please either scan with your QR reader or click on the QR code to take the lab progress survey. It expires on 11/2/2018 at midnight. I am currently updating my image of Kali to version 2 and testing. It should be ready by Friday.
Pre-Lab Survey
Please follow this link to complete a pre-lab survey. There are no right or wrong answers. This is simply to assess your knowledge of wireless security prior to completing this project.
((This survey is only for Spring 2019 students!))
The Scenario
Each group is a company that specializes in penetration testing focusing on wireless and web security. Your company has been hired by Kennesaw State University to pen test the “KSU Wireless Security” network and “KSU Raspwn” the Graduate Research Web Servers for the College of Computing and Software Engineering.
Project Management
Your instructor is the project manager for your company. Here are your deliverables.
-
- Students will place themselves in a group on D2L
- Groups should be no less than 3 students and no more than 5
- Identify a Team Lead for your group
- Only the Team Lead will communicate with the Project Manager
- Give your group a company name
- Establish roles within the group (2 Researchers, 2 Pentesters, and 1 Team Lead)
- Researchers will research the tools listed in each step
- Pentesters will use the tools researched in each step
- Team Lead will gather all documentation and put together the final report
- The “Company” will be prepared to present its findings to the Project Manager
The Project
Step 1 – Compare and Contrast Pentesting Platforms
Research and compare 3 out of 4 of the following penetration testing platform: Kali, ParrotS, BlackArch and Pentoo.
You have two options:
- List 5 pros and 5 cons between the 3 of the above platforms.
- Create a table listing 10 features and compare the features of the 3 platforms. Please see this example.
Step 2 – Research and use Wifi WPA Auditing Tools
Research Fern Wifi Cracker and Wifite. These are two tools that can be used for wireless auditing and perform essentially the same task. One is GUI, the other command line. Use one of these tools to obtain the password and connect to KSU_Wireless_Security SSID. Document your steps in a word document.
Update 11/7/2018 – It has come to my attention that some of you would like to use your own systems to complete the assignment. This is perfectly fine, however, without my custom wordlist, it would take you over a decade using any dictionary of your choice. You can follow this link to download my dictionary. https://drscotland.com/wl/ksuwordlist.zip
For my super smart students who are thinking, “I can just open the wordlist and find the password!” You should know that I am two steps ahead of you. The world list is 100mb and even with a dual-core 3.5Ghz processor and 16gb of ram, it will freeze your system. Learn how these password cracking tools parse data to be able to read one line at a time without crashing a Raspberry Pi. Have fun!
Step 3 – Research and use Information Gathering and Vulnerability Analysis Tools
Research SPARTA and nmap. These are both tools that can be used for information gathering and vulnerability analysis. The perform essentially the same task. One is GUI, the other command line. Use one of these tools to scan the KSU Raspwn network for hosts and open ports. Document your steps in a word document.
Step 4 – Research and use Exploitation Tools
By this point, you should have discovered all hosts on the network, open ports, and identified what service or server is running on those hosts.
The tools in this area are very broad. In order to be great at penetration testing, you have to identify the tool that will provide you with the best results. Those results may include, information gathering, exploitation, and reporting all in one tool.
Research Armitage and Metasploit Framework. These two have been selected as they work together in exploiting vulnerabilities. Both are GUI and resource intense. Do not run both at the same time on the Raspberry Pi. Use one of these tools to scan ONE of the hosts that you identified as vulnerable in step 2. A “Hail Mary” may not be to your advantage on a Raspberry Pi. Nor is it a stealthy approach. Document your steps in a word document.
Step 5 – Putting It All Together
You have completed your research, pen testing, and documentation in steps 1, 2, 3, and 4. Your documentation was for the purpose of creating a PowerPoint.
Create a PowerPoint covering the following:
- How did you come up with a team name
- Who are the members of your team and their roles
- Why were these team members selected for their roles
- Which tools did you select for each step and why
- What challenges were there as a team or individuals
- Suggestions for future students
- Questions
Post-Lab Survey
Please follow this link to complete a post-lab survey. There are no right or wrong answers. This is simply to assess your knowledge of wireless security after completing the course and lab.
((This survey is only for Spring 2019 students!))
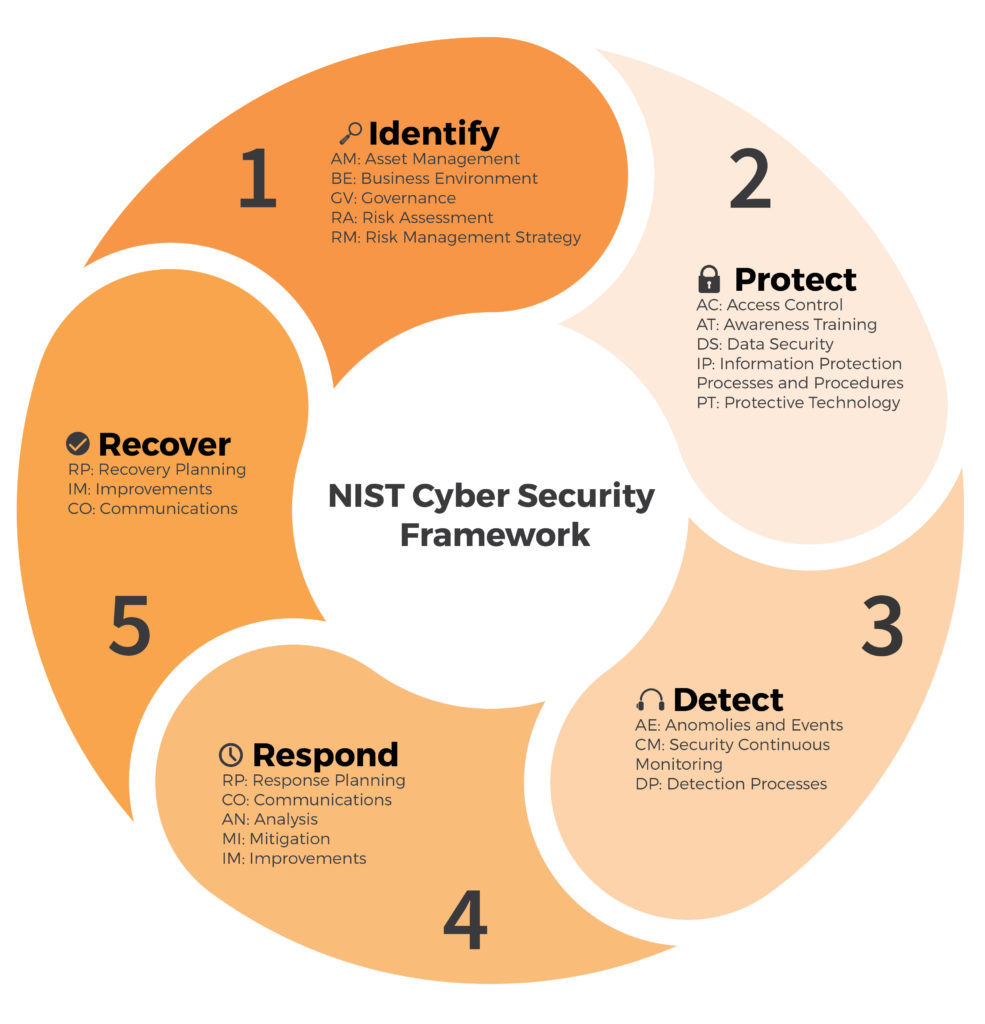
Future Work (Possibly Capstone)
Use the NIST Cybersecurity Framework to put it all together and be prepared to present to the class and possibly outside employers in the cybersecurity field. Create a 10-page PointPoint in which you address how you would use the NIST Cybersecurity Framework to protect a real organization based on this lab.
WARNING – It is possible to connect eth0 to the internet and use RasPwn as a (possibly the world’s most insecure) wireless router, however, IF YOU DO SO PLEASE DO SO FROM BEHIND NAT AND A FIREWALL! DO NOT EXPOSE ANY RASPWN INTERFACES DIRECTLY TO THE INTERNET OR FORWARD INTERNET TRAFFIC TO RASPWN IN ANY WAY!!!
